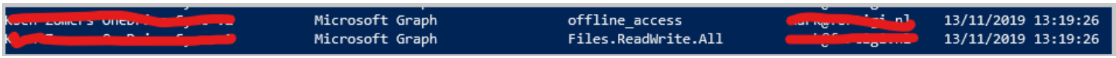
Oauth credential fishing is a problem for Microsoft 365 customers. The recent hack of 28.000 e-mails at SANS shows this can even happen to companies that give security training. Although mitigations might be costly or time consuming detecting this attack is not as hard as you might think. Using MS Graph you can query all apps that users consented to as well as which permissions where granted. Any app that requests mail.read, mail.readwrite, files.read, or files.readwrite and is consented to by a user should raise suspicion.
I wrote a small PowerShell script that will show you exactly which users consented to which apps with which permissions. Something like this should scare the shit out of you… unless you know what it is;
Did you know you could also set notifications in Azure AD when this happens… using the eventhub and logic apps.. this is a cheap way to at least get a notification when this happens? I'll try to do a blog post on that later..